It is More Than Just Internet – It is How Business is Done
A connection to the internet is no longer a luxury, it has become an absolute necessity to do business. How we as business owners view our internet connections will play a major role in their ability to provide the connectivity, reliability, flexibility, and security required to operate the day-to-day applications. This document is intended to review the different types of internet, the benefits, geographic considerations, the providers, and the limitations of each.
It is important to note the very process and methodology for acquiring internet service has changed. In the not-so-distant past, the RBOCs (Regional Bell Operating Companies) were obligated by the federal government (FCC) to provide voice and data connectivity to any valid address within their region. If the carrier had to build infrastructure to a new residential or commercial address, they were not able to pass the cost on to the customer. The pricing was regulated by “Tariffs”. With the increased demand for bandwidth, the carriers have petitioned the FCC requesting the ability to retire the legacy copper networks in favor of moving to the much faster fiber optic infrastructure. With the permission to retire the older copper networks came the release of the obligation of providing infrastructure.
What this means to business owners is in a growing number of geographic locations internet pricing is no longer regulated. Acquiring voice and data connectivity has now moved us to a competitive bid process. With many carriers retiring the legacy copper networks, a fiber optic connection may be the only terrestrial option. To add insult to injury, there are many geographic areas including large business parks where fiber optic cable has not yet been deployed and, in many cases, may not be deployed for months or years after a business has moved in. Businesses may request pricing for a fiber optic connection and receive a quote that includes build costs upwards of $ 10,000.00 dollars or more. This scenario may leave the businesses options limited to point-to-point wireless, satellite, or cellular.
It is also important to note situations like these are not limited to new construction or to rural areas. Depending on the fiber distribution plan of the carrier or carriers, businesses in major metropolitan cities may still be a great distance from affordable fiber optic infrastructure. Even though copper may still be available in these locations, the speeds and reliability of the connection is limited to the carrier’s willingness to maintain the service. Many carriers are balancing their finances by abandoning maintenance of the copper infrastructure and retiring the training processes for technicians. As the older technicians with experience on the legacy copper networks retire, the ability and willingness of carriers to maintain technical staff retires with them.
CT Solutions believes it is important to identify a business’s internet requirements, acquire a comprehensive list of available carriers to the specified business address, and what internet products are offered by the available carriers before ordering any services. Many times, the ability to identify carriers outside the locally advertised providers will require contracting a “Technology Architecture”, “Technology Consulting”, or “Trusted Technology Advisor” like CT Solutions. CT Solutions works with an estimated 3,000 local, regional, national, and international carriers to provide our clients with technology solutions as unique as each business.
In many cases, CT Solutions may be able to identify carriers with the ability to provide “Type 2” connectivity and substantially enhance the product and or service portfolio with competitive price points.
The following is an overview list of internet product types along with a list of issues each business should address before selecting a carrier and ordering service.
Commonly Advertised Internet Services:
Broadband – This is typically the least expensive internet service option. Carriers may have a number of different product speeds and pricing models. In some cases, carriers will bundle additional business services such as voice, wi-fi, and a managed router option with package pricing. This term has three (3) significant impacts on the circuit’s performance expectations.
1. It is a Shared Service.
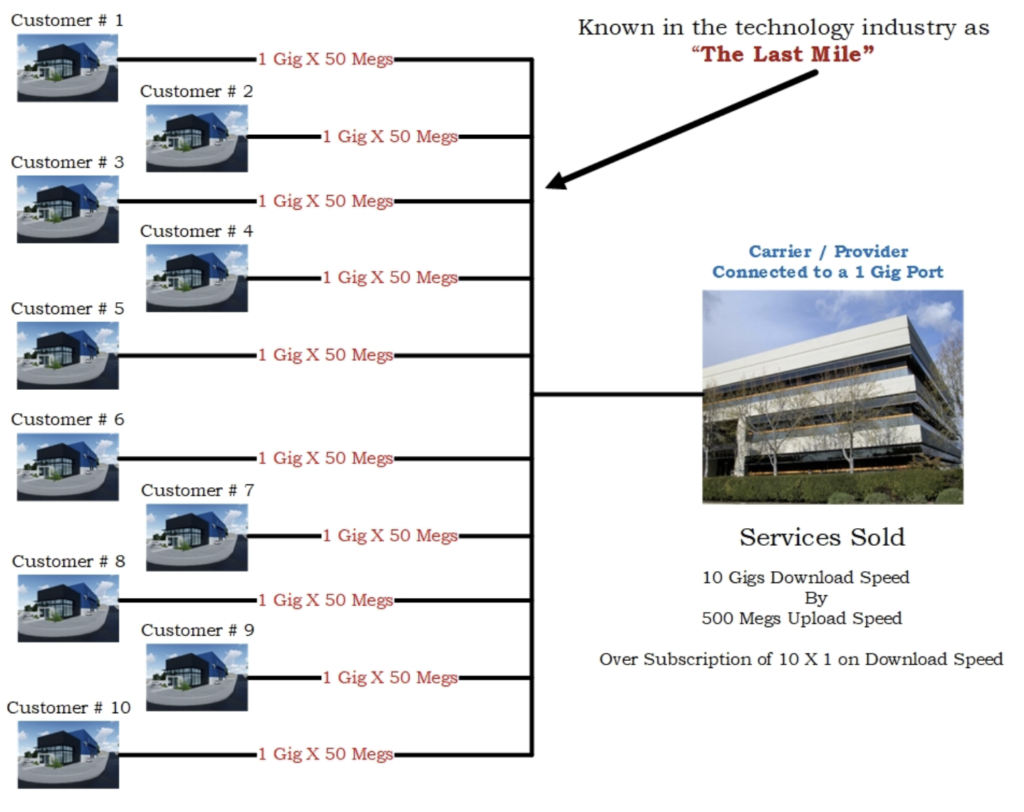
The image above shows a 10 to 1 over subscription on the downloading speed. Over subscriptions can be as much as 100 to 1 with number of carriers. The contracted internet speed refers to the maximum capabilities of the “Last Mile” circuit connection. The “Last Mile” refers to the connection between the customers specified address and the connection point / POP (Point of Presence) for the carrier.
2. Most Broadband Services Do Not Carry SLA’s (Service Level Agreements).
Any SLA’s will be based on up-time and not QOS or (Quality of Service). Example: If a business purchases a 1 gig download X 50 megs upload circuit and only gets 300 megs download speed, X 20 megs uploading speed, there is no assumptions of credits or other compensation for the variance in service delivery. This is known as a “Best Effort” agreement.
3. In Most Cases, The Circuit Will Be A Synchronous vs. Synchronous.
A Synchronous refers to the difference between the download speed and the uploading speed. Broadband fiber circuits may be closer to the same speeds down and up.
Broadband services are commonly delivered in the following formats:
- Copper / DSL
- Copper Cable Internet
- Point-to-Point Wireless
- Satellite
- Cellular
Dedicated – The product name for this service varies between carriers but will typically be offered at a much higher price point. Dedicated Internet Access (DIA) will be provisioned on a one-to-one ration. Dedicated services will most likely be delivered via fiber optic but in some areas and depending on the required speeds, they may still be delivered via copper on a Metropolitan Ethernet Circuit.
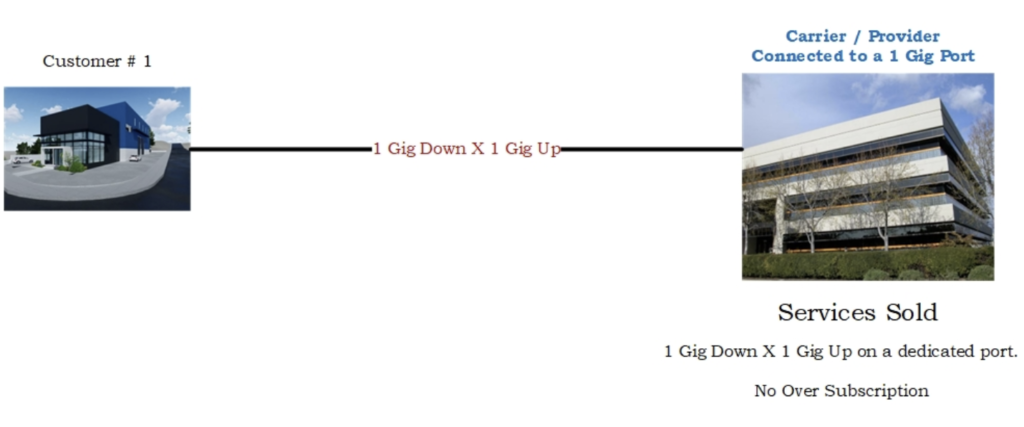
DIA usually comes with an 80% SLA (Service Level Agreement). If at any time the service drops below the minimum speed allowed within the contract, the carrier has a designated time point to bring the circuit back up to contracted speed or the customer is entitled to financial compensation. Financial compensation is typically credits off the monthly invoice for every specified block of time the circuit remains out of contracted range. Dedicated circuits are often delivered on carrier provided managed routers. This allows the carrier additional access to monitor and manage the circuit. This configuration requires the customer to call the carrier’s technical service support number to make any programming changes to the router.
DIA can also be delivered via a simple ethernet or fiber optic handoff from the carrier’s premise equipment directly into the customer’s firewall. The customer would be responsible for programming, monitoring, and managing their own network while the carrier maintains the ability to monitor and test the circuit to the carrier equipment within the customer’s IT room.
Designing The Circuit:
Allow for Growth – CT Solutions always encourages customers to consider growth when ordering any carrier-based service. When designing current bandwidth requirements and pricing an internet circuit, CT Solutions recommends requesting pricing for a couple bandwidth speeds above the target speed. This will allow you to acquire the design of the circuit.
To provide an example, Let’s assume you are looking for a 1 Gig dedicated fiber internet connection. You request pricing from a carrier. You receive the following quote.
- 1 Gig Fiber Connection – 36 Month Agreement
- Monthly $ 756.95 – Install $ 250.00
You sign the agreement, and the circuit is installed. Six months after the circuit is installed you purchase another business and need to incorporate all the staff, and internet-based business applications into your network. The additional business applications will require you to double your internet capacity, so you contact the carrier and request a price to double the bandwidth on your circuit.
What you will receive is a quote for a whole new circuit. The quote will be for 2 Gigs on a 10 Gig port. The first 1 Gig circuit you purchased was terminated at the carrier’s data center on a 1 Gig port not allowing for any growth. CT Solutions recommends if you are in the market for a 1 Gig circuit that you always inquire what size port it is terminated on to verify your business’s ability to grow.
IP Addressing
DHCP – Many internet services are delivered with DHCP (Dynamic Host Configuration Protocol) connectivity. This is an IPV4 address that is rented for a temporary period of time. It is available during a network traffic session. It is subject to change as the demand for network sessions increases. This protocol works well for temporary business applications such as surfing the web, sending, and receiving email, or even making a (VOIP) Voice Over Internet Protocol, business call.
Static IP – Other business applications may require a static IP address. Static IP addresses are assigned to the customers network and never change. Some applications that may require a static IP are VPN (Virtual Private Network(s)), POS (Point of Sale), video surveillances
systems, and network monitoring and management software tools.
CGNAT – It is important to understand a growing number of voice and data carriers are running out of IPV4 addresses.
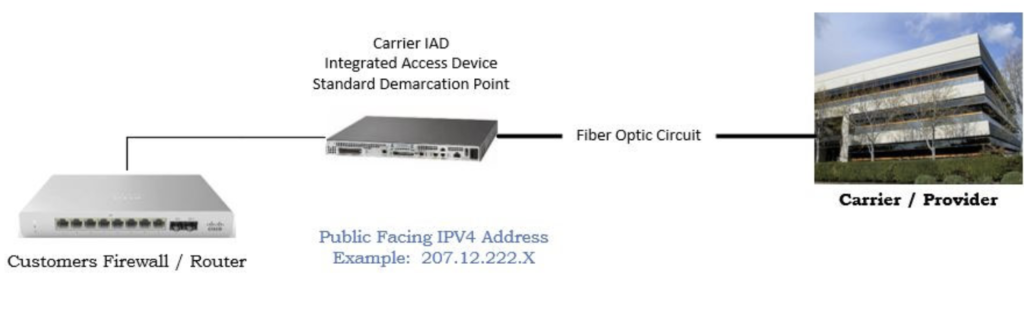
Directly below is a simple diagram of a standard Static IPV4 network handoff showing a public facing / public routable IPV4 address. In this scenario, the “Carrier IAD” is the point of demarcation. The customer assumes responsibility for the network at the WAN (Wide Area Network) cable. The customer would use the “Public IP Address” 207.12.222.X to provide routing functionality for their business applications.
In the diagram below the “Customers Firewall / Router” is receiving a private (Non-Public Routable) IP address. This is known as CGNAT. The customer has no control over the “Carrier Owned Premise Router” Any applications requiring “Port Forwarding” will no longer function.
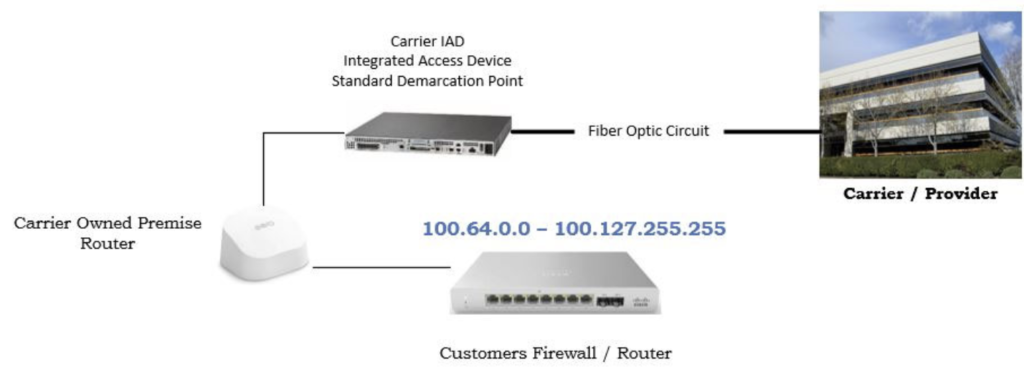
All outbound traffic will function as usual, but CGNAT can affect applications requiring data verification and other in-depth security and quality assurance protocols. CT Solutions recommends customers requiring public facing IP addresses verify with the carriers they are able to receive a true routable IP address before completing an order. (CT Solutions has alternative solutions to resolve CGNAT issues. Carriers that are using CGNAT will not be able to provide blocks of IPV4 addresses without possible additional
monthly charges or may not even be able to provide the service with additional fees. In these scenarios, the customer could choose to investigate a “Type 2” provider that still has IPV4 addresses to sell or begin to use an IPV6 network strategy.)
IPV6 – This IP addressing scheme (Protocol) was developed to address the depletion of the nearly 4.3 billion IPV4 addresses around the world. An IPV4 address consists of four (4) octets of eight (8) bits each totaling 32 bits. The IPV4 addresses are based on a binary
addressing scheme. An IPV6 address consists of eight (8) segments of sixteen (16) bits totaling 128 bits in a hexadecimal addressing scheme.
From CT Solutions’ experience the carriers are split about 50/50 in those that are currently providing both IPV4 and IPV6 addresses. There are still a large number of cloud-based applications such as UCaaS (Unified Communications as a Service), FTP (File Transfer Protocol), and even POS (Point of Sale) providers that have not\ migrated to an IPV6 ready platform. CT Solutions believes it is important to ask the IPV6 readiness question to both the carriers and the application vendors to ensure the network is not obsolete before it is even completed. If your business has the opportunity to start moving applications over to an IPV6 platform, you will put yourself in a proactive posture and avoid crisis at a later point.
What is a “Type 2” Service? – A “Type 2” circuit is when a third-party carrier purchases a passthrough circuit from a provider local to the customer and terminates the circuit onto the network of the “Third-Party Provider.” It is important to note in this scenario, all network services are delivered, monitored, and managed from the network of the “Third Party” provider.
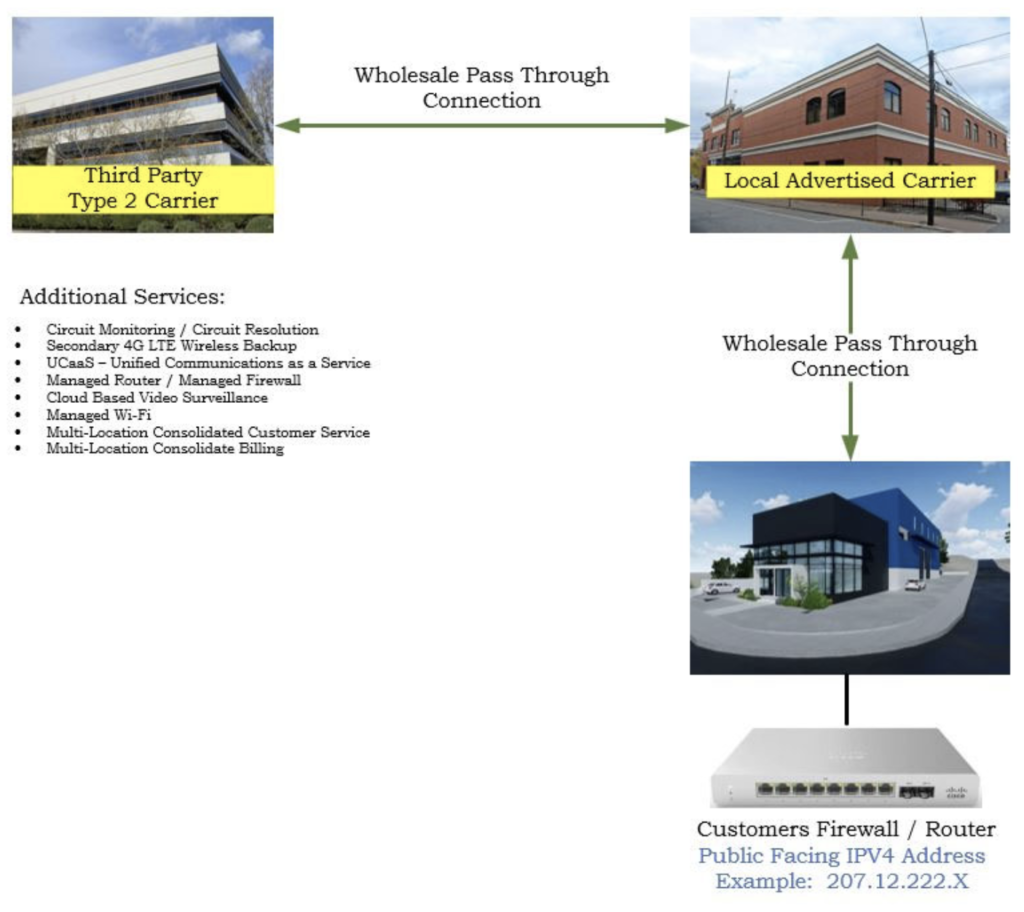
Type 2 circuits can greatly enhance a business’s technology options by expanding the product & service portfolio beyond the standard generic menu.
- Reason # 1 to explore “Type 2” services might be acquiring a public facing static IP address from the “Third Party” provider when the local provider is not able to provide one.
- Reason # 2 to explore a “Third Party” “Type 2” provider might be network security services through a SOC (Security Operation Center).
- Reason # 3 to explore a “Third Party” “Type 2” provider is additional business services such as:
- Circuit Monitoring / Circuit Resolution
- Secondary 4G / 5G Wireless Internet Backup
- UCaaS – Unified Communications as a Service Business Voice / Telephone System
- Managed Router / Managed Firewall
- Cloud-Based Video Surveillance System
- Managed Wi-Fi
- Multi-Location Consolidate Customer Service
- Multi-Location Consolidated Billing
- Reason # 4 to explore a “Third Party” “Type 2” provider is buying power and customer service. Let’s say you were to go to your local carrier and attempt to order a fiber service. The local carrier states the fiber is too far away to build to your address until they have ten (10) additional customers in your area. The monthly charge for the service you’re attempting to order may be between $ 500.00 and $ 1,000.00. A “Third Party” provider may have 1,000 circuits with that same local carrier and their monthly billing is $ 500,000.00 to $ 1,000,000.00. When the “Third Party” provider goes to the local provider and orders a circuit, their chances of motivating the carrier to install the service are much greater due to the much larger amount of business.
Reselling a Service – There are occasions a “Third Party” carrier will not purchase a “Type 2” circuit but just resell the local providers services. This typically happens in scenarios where the customer has multiple locations, and the desired benefit is consolidated billing. The “Third Party” carrier becomes the customer of record for the local carrier and in some cases is able to demand stronger SLA’s than the customer who is receiving delivery of services would be able to secure.
An Important Diversion – For over 50 years, analog lines have been a staple in voice connectivity due to the low voltage current supplied by the carriers. In the event a business location had a power outage, the business was still able to pick up the phone and dial for emergency assistance if required.
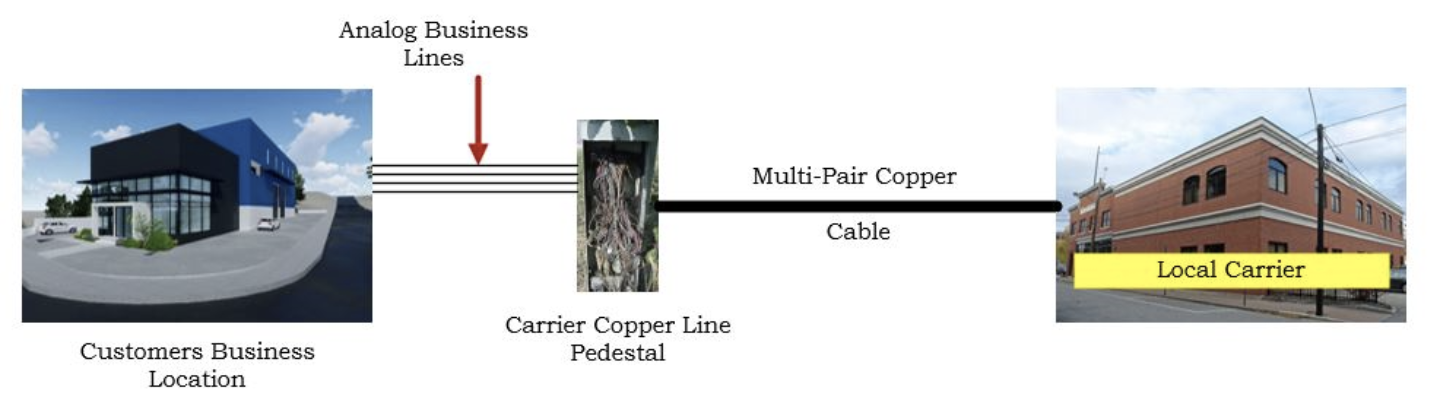
This is the primary reason analog lines were required in multi-tenant building emergency elevator phones, fire alarms, and even burglar alarm systems.
As stated at the beginning of this document, the carriers are retiring the analog networks. There are two primary reasons behind the carrier’s decision to do this.
- Too expensive to maintain.
- The demand for bandwidth is much greater than the legacy copper network’s ability to deliver.
The results of this decision are far-reaching and will have a greater impact on businesses going forward.
- Training for analog technology is being discontinued.
- Parts for analog systems have become and will continue to become more difficult to acquire.
- Pricing for analog products will continue to increase to encourage businesses to migrate to less expensive IP based business applications.
Although analog lines are still listed as available through some carriers, chances are they are only “Terminated” as analog. The difference between actual analog and lines that are terminated as analog is low voltage power is absent in the lines that are terminated as analog.

Lines that are “Terminated” as analog are translated to an IP signal through a device known as an ATA (Analog Telephone Adapter) which requires power to operate. The benefit of acquiring dial-tone for an emergency call is no longer a reality and the difference in pricing is minimal if any.
CT Solutions acknowledges there are a number of legacy business systems that may prove too expensive or may not even provide options to update / upgrade from analog connectivity to IP. It is important to note the performance, security, and overall functionality of any such equipment can be compromised when terminated on a circuit that simulates an analog connection vs. an actual analog line. True analog lines are still available in some areas but note the maintenance of these lines is not the carrier’s priority and will be phased out completely over the next few years.
Phone service is one business application that should be converted to an IP platform immediately rather than wait until analog services are no longer available. Pricing for IP based voice services is right in line with the cost of analog dial-tone, offers a much greater feature benefit package and illuminates the need for additional equipment such as analog telephone adapters. In summary, there is no remaining benefit of hanging on to analog voice services.
Network Access Strategies
Due to “Digital Transformation” every business owner will need to define their “Business Network Access Strategy”. Everyday, more business applications are connected to and rely on some type of data network connection. Turning a blind eye to the fact that a connection can and will malfunction or completely fail at some point will only amplify the cost and the difficulty of recovering once it does.
The following is a list of “Network Access Strategies” starting with a reactive response and migrating up to an aggressive proactive posture. These are provided for the evaluation of each business owner and the long-term effects their “Network Access Strategy” will have on their business.
Simple Plug & Play (Reactive Posture)
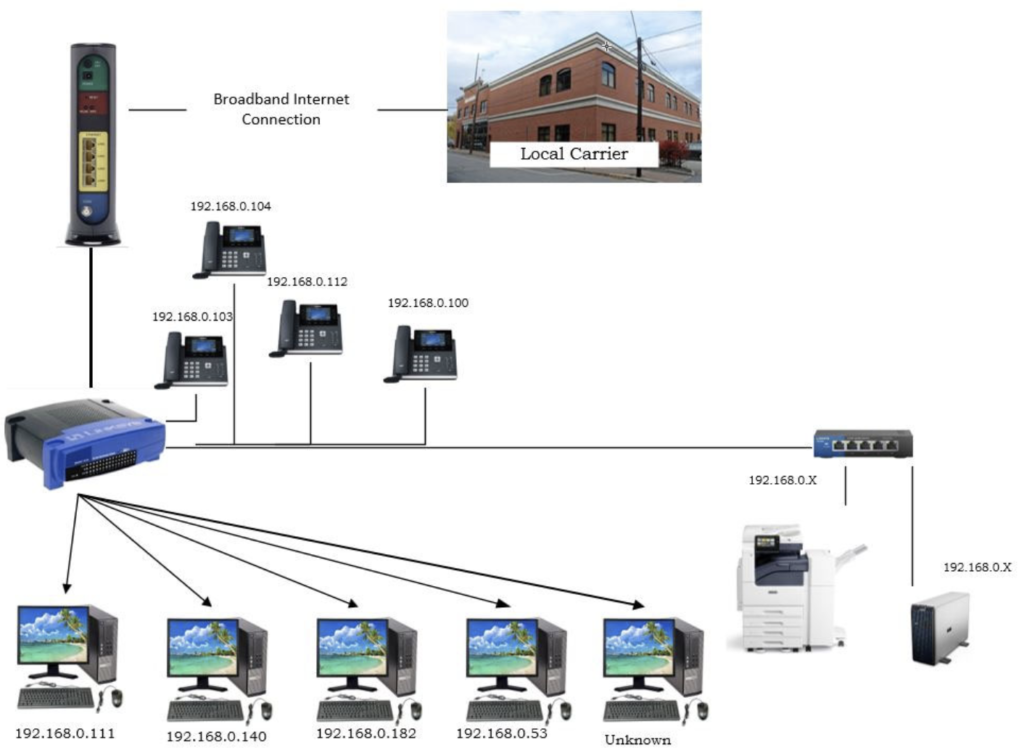
This is the most entry level “Network Access Strategy”. Customers call the local advertised network carrier to order internet service to their business address. Here are some potential results based on previous experiences:
- Multiple network service options are available at varying price points and the customer is able to order a service and get it installed within a reasonable time.
- The business address is in a new construction, the carrier may not have the service available for an undetermined period. Business would be forced to explore alternative options such as satellite, point-to-point wireless or cellular.
- The business address was previously occupied. When the previous business moved out, the carrier decommissioned the copper network infrastructure that serviced the address. The carrier would be willing to offer fiber infrastructure to the address, but the building cost will require a large upfront cost and service will not be installed for 90 – 120 days minimum.
How Can CT Solutions Help?
CT Solutions works with an estimated 3,000 local, regional, national, and international carrier providers. If / when your business is looking to acquire “Network Access” CT Solutions can assist you to identify which carriers are able to provide service to your business location, which products are available from each carrier, and at what price points. CT Solutions encourages any business looking to relocate or open a new location to survey network accessibility before signing a lease or purchase agreement.
Let’s assume the business is able to acquire a broadband internet service. They order a VOIP (Voice Over Internet Protocol) phone system and a couple (POS) Point of Sale computer workstations and open their doors for business. Everything is going as planned until one morning, the manager comes in 1 hour before the business opens its doors and the internet down. What happens now?
- Has the store manager been trained to trouble shoot network outages?
- Do they have access to the network providers customer / technical service telephone number?
- Will they have access to a phone to make the call to technical support?
- Will they need to use their personal cell phone with their personal caller ID associated with the call?
- Will they need to provide their personal cell phone number for a call back in the event the call gets disconnected?
- Does their cell phone have sufficient battery life to remain on hold for the necessary time period to complete the technical support call?
- Do they have access to the businesses account number?
- Are they authorized on the businesses account to open trouble tickets?
- Authorization of management staff can be cumbersome and, in many cases, forgotten if frequent staff changes occur.
- Do they know the physical location of the carrier’s modem / router?
- Do they know how to test the circuit from the carrier’s modem / router?
- Is there an additional router / firewall owned by the business that needs to be tested?
- Does the manager focus on getting the internet back up and functioning or preparing the rest of the business to open?
- What happens if the internet is not working when the business opens?
- How many customers will not be able to reach the business because the phones aren’t working?
- How many credit / debit card transactions will not be able to be processed because the internet is not working?
- How many employees will not be able to do their job because the internet is not working?
- What is the cost of the lost productivity?
Circuit Monitoring / Circuit Resolution (Proactive-Reactive)
This is a service that can be ordered to monitor network access circuits 24/7/365. In the event the circuit goes down, a trouble ticket is automatically opened with the carrier to get the repairs started immediately. The customer receives an email stating the circuit is down and the trouble ticket number from the carrier. The customer is kept up to date on the progress of the repairs throughout the entire process.
- The customer signs a LOA (Letter of Authorization) providing the service provider with permission to open the trouble ticket eliminating the need for staff to be authorized on carrier accounts.
- The LOA contains the customers account number and the customer service / technical support phone number of the carrier eliminating the need to look them up in an outage situation.
- The technical support call is being made from a “Network Operation Center” associated with a professional business and not the personal cell phone number of a company staff member.
- The technical support call is being made from an industry trained knowledgeable staff member with the ability to communicate at a level to assist the carrier resolve the issue.
4G / 5G Wireless Backup (Proactive)
Introducing a 4G / 5G wireless cellular service to your business network provides a secondary network access option in the event the primary circuit becomes non-operational. There are multiple ways to configure this option and multiple pricing structures as well. We will discuss a couple of different options and their effect on both network operation and the financial dynamics as well.
Usually, the 4G / 5G wireless access device will need to be placed into what is known as a “Passive” position on the network. The term “Passive” indicates the device is not providing network access until or unless the primary circuit fails. Depending on the features and functionality of the location router / firewall, the router should be able to monitor both the primary and secondary WAN (Wide Area Networking) ports to determine if any data traffic is passing through. In the event data traffic stops on the primary WAN port, the router should automatically open the secondary WAN port so external data traffic will continue to flow. In addition, the router should send an alert notification to the network administrator notifying them the primary circuit is down and the system is running on the secondary access.
** Important Notes
When purchasing a 4G / 5G data plan as a data backup, it is common practice to select the entry level plan. Plans start at around $ 35.00 monthly and typically offer between 2 Gigs to 5 Gigs of data. (Prices and data plans will vary depending on geographic location and selected cellular provider)
- Depending on the plan purchased, if the data exceeds the amount included in the purchased package the customer may be charged much higher rates for “Overage” data or the plan will be shut down completely until the next billing cycle.
- Depending on the feature capabilities and programming of the router / firewall, once the primary circuit is repaired and functional, the router / firewall may automatically switch the traffic back to WAN port 1 off the 4G / 5G circuit.
In the event the location router / firewall does not have the capability of two (2) WAN ports, placing the 4G / 5G router in front of the firewall places the responsibility of monitoring the inbound / outbound data traffic on the 4G / 5G wireless appliance. There are a number of devices capable of passing terrestrial broadband circuit traffic through to a premise-based firewall for normal data traffic operation and monitoring. In the event the primary circuit fails, the 4G /5G router is already in line to activate the cellular data plan and keep the business up and running.
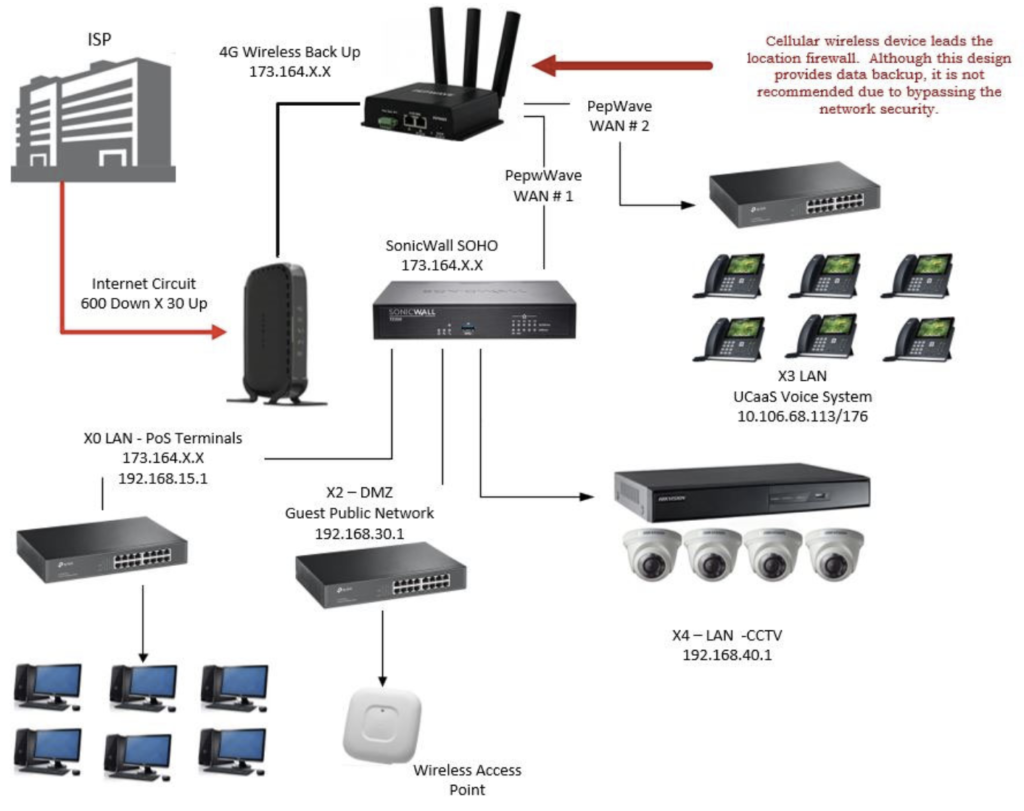
Although this design provides for a secondary network connection, it is not recommended. This design creates a serious network vulnerability by bypassing the functionality and network policies of the primary router / firewall.
Consider A Strategy of Multiple Strategies (Proactive)
Due to the secondary internet (Network Access) allowing businesses to continue functioning when the primary internet circuit is down, a common area of shock and frustration is extremely large invoices from the cellular carriers due to data overages. All to often, the minimal monthly cellular plans are selected with the intent of keeping the total monthly budget low. When the primary circuit goes down and business continues as usual without any type of throughput monitoring, the overage charges can add up quickly. CT Solutions recommends combining “CMCR” (Circuit Monitoring, Circuit Resolution) with the 4G / 5G wireless backup to get the primary circuit back up and operational as quickly as possible and minimize the possibility of large overage charges. Another recommendation is to ensure outage alerts are established on every circuit to notify a member of the technical staff if / when a circuit goes down. Once notified of an outage, the technician should be engaged throughout the recovery process and verify the network traffic is once again flowing through the primary terrestrial circuit.
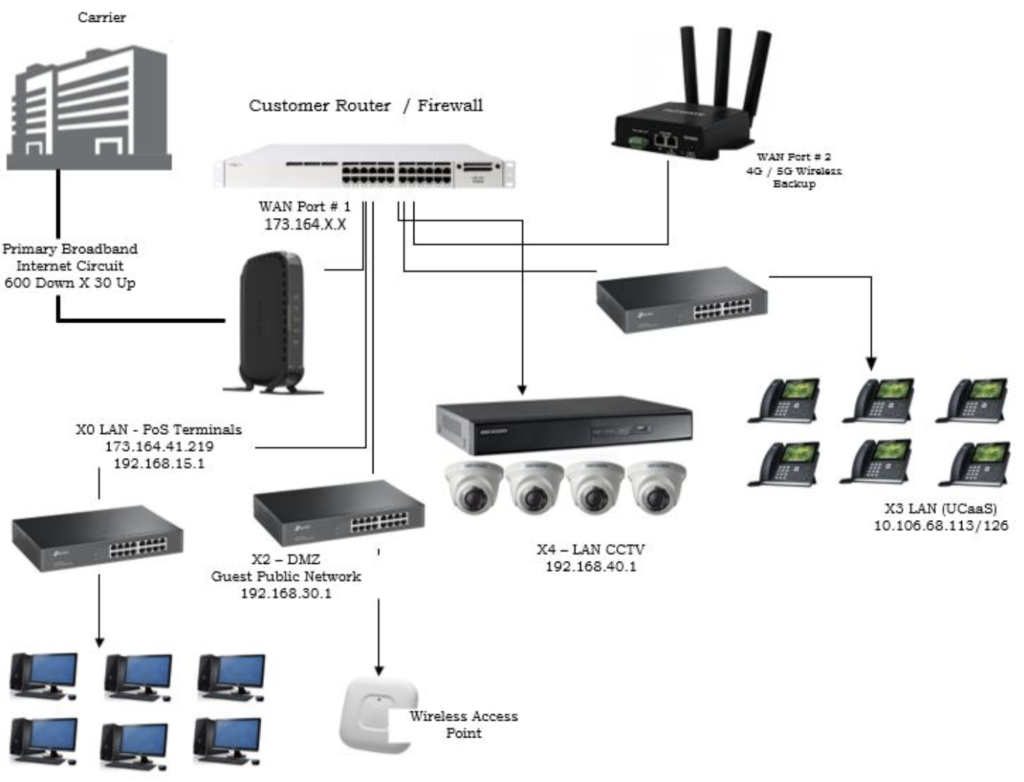
Managed Network (Proactive)
Managing the network is a “Proactive” strategy that goes beyond just the internet. Managing a network can be accomplished through a growing number of carriers, internal staff or an external MSP (Managed Service Provider), or MSSP (Managed Security & Service Provider).
Below is an illustration showing the different parts of a network that can be managed. A growing number of carriers and third-party vendors provide GUI (Geographic User Interfaces) that consolidates the management of multiple applications on to a single platform.
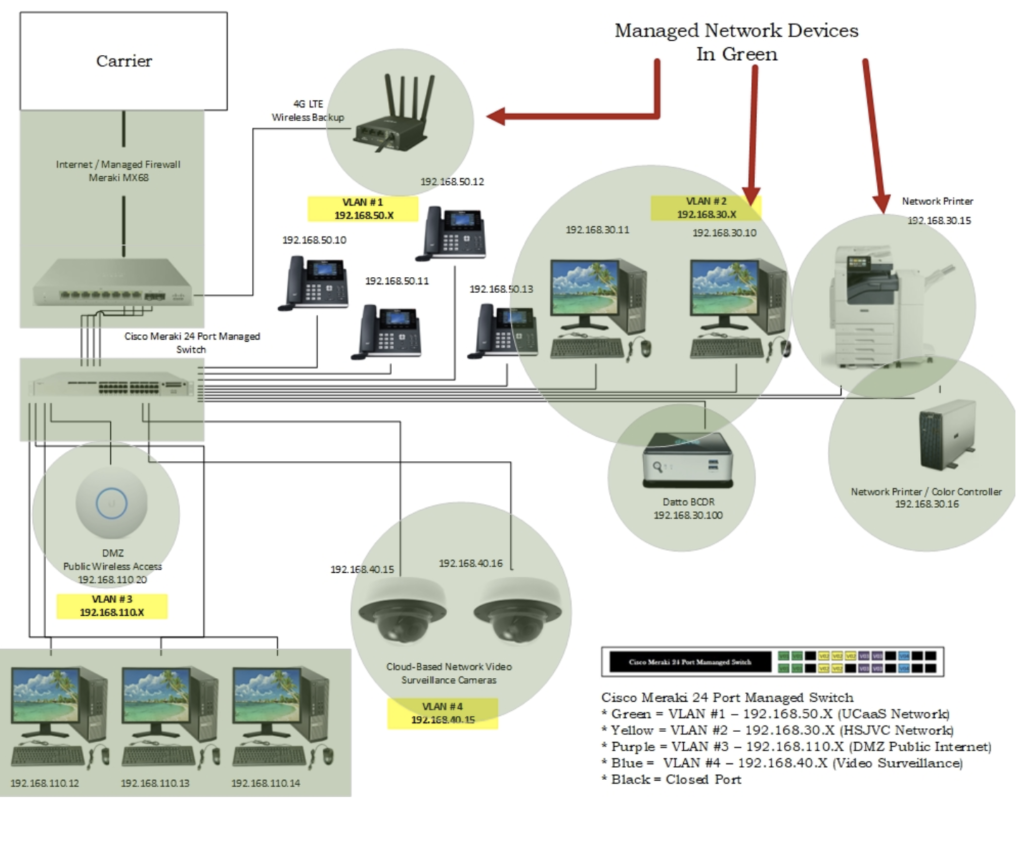
Network management can be controlled completely by the vendor, or co-managed between internal IT staff and a vendors NOC (network Operation Center) or SOC (Security Operation Center). It should be understood that unless the equipment has been manufactured with the ability to be monitored and the monitoring features have been turned on, monitoring and managing will not be possible. If this is an option you and your company wish to utilize, check the feature list of any equipment you are looking to purchase or is already a part of your network for the SNMP (Simple Network Management Protocol) or like capabilities. Pricing for network monitoring and management will vary drastically depending on the number of devices, number of locations being managed and the schedule. The term “Schedule” refers to “Time of Day, Day of Week” agreement and the expected response for any alert. Monitoring for M/F 8:00 AM – 5:00 PM will run at one price point while 24/7/365 will run at a much higher price. In addition, a management agreement will specify if any on-site service is required or if the agreement is strictly based on remote services.
SD-WAN (Proactive)
SD-WAN otherwise known as (Software Defined-Wide Area Networking) is the technology industries top shelf solution. SD-WAN provides an opportunity for a corporate network to have all the redundancy, monitoring, management, and reporting bundled into a single service.
Redundancy – Many SD-WAN network access devices allow up to four (4) connections that have multiple configuration capabilities. Here are some examples:
Primary Connection
o Dedicated Fiber – 500 Megs Down X 500 Megs Up.
o Circuit Status – Active
Secondary Connection
o Broadband Fiber – 200 Megs Down X 200 Megs Up
o Circuit Status – Active
Tertiary Connection
o Broadband Copper Cable – 500 Megs Down X 50 Megs Up
o Circuit Status – Passive
With the “Primary” and “Secondary” circuits being active, the businesses “Network Access Gateway” would have a combined available bandwidth of 700 Megs Down X 700 Megs Up. In the event either the primary or the secondary circuit were to fail, and data network secession would continue without interruption by automatically switching over to the circuit that remained functional.
In addition, the passive circuit would switch to an active position and a trouble ticket for the failing circuit would automatically be created with the carrier to get repairs started immediately.
The next level capability of an SD-WAN service is traffic shaping and reporting. SD-WAN allows for application prioritization by percentage of available bandwidth or specific bandwidth amount.
Example:
1 Gig of total bandwidth available:
- UCaaS (Unified Communications as a Service) Priority Level 1
- 100 Megs of total bandwidth or 10 % of available bandwidth
- POS (Point of Sale) Priority Level 1
- 50 Megs of total bandwidth or 5% of available bandwidth
- Web Server (Online Orders) – Priority Level 2
- 300 Megs of total bandwidth or 25% of available bandwidth
- Email – Priority Level 3
- 50 Megs of total bandwidth or 5% of available bandwidth.
Monitoring, Management, & Reporting – SD-WAN provides the ability to monitor the network access gateway with multiple real time and historic data reports. Alerts and reporting can be established at specific levels of circuit degradation to open trouble tickets and notify technical staff. SD-WAN is a powerful tool for businesses of any size. For small businesses relying on network connectivity for POS, online orders, and business voice services, SD-WAN allows an extra layer of reliability, analytics, and management. For multi-location global enterprises, SD-WAN can serve as a cost-effective topology for secure location-to-location connectivity with an overlay of monitoring, management, flexibility, and security.
Let it be stated, this is only a brief overview of the capabilities of SD-WAN. There are a growing number of carriers offering SD-WAN and each provides their own twist. In most cases, network security is an add on product but a few carriers that specialize in network security utilize SD-WAN as the method of transport between the customers premise and the SOC (Security Operation Center). The internet is not introduced to the customers network until the data traffic hits the SOC thus creating an encrypted and private data tunnel.
Cloud (Proactive)
When a business makes an attempt to bullet proof their data network, it does not take long to determine, it is expensive. When comparing cloud-based computing vs. off the shelf consumer grade network connectivity, cloud-based will always be more expensive. Realistically, there is no real apples – to – apples comparison.
** Note – DSL (Digital Subscriber Line) was created with the in-home (Residential) on-line gamer in mind. DSL was also the first “Broadband” technology available to the general consumer. It was intended to be a residential product. Before DSL, an on-line gamer or a grandmother wishing to see a picture of her newborn grandbaby would use a dial-up connection with an over subscription rate in the neighborhood of 35 customers to 1 modem. When the consumer was done with playing their game or receiving their electronic mail, the
computer and the modem were disconnected.
In contrast, businesses would purchase very expensive point-to-point private circuits that were priced based on mileage. It was not uncommon for a 1.5 Meg circuit to cost in the area of $ 2,500.00 – $ 4,000.00 monthly with a $ 10,000.00 or more install. (The prices I have listed here were very common but realistically, circuits from coast-to-coast could easily be in the neighborhood of $ 10,000.00 per month and more.) In addition, the installation process would take four to six months. In many cases, these private circuits were built to accommodate a single business application such as FTP. (File Transfer Protocol) In the event, a business wanted to add another application to their network, they were faced with the additional cost of another point-to-point circuit.
Connecting a multi-location company with point-to-point private circuits was labeled as an “Intranet” vs. the “Internet” we know today. With an “Intranet” any cyber threats were limited to within the boundaries of the private corporate network where as today, cyber threats can and do originate from anywhere around the globe.
Cost reduction was a large motivator for the development of shared network protocols such as X.25, Frame Relay, ATM, and MPLS. Although these services were still priced out of reach of the consumer and the SMB (Small to Medium Business) owner, the ability to utilize a single network connection for multiple business applications had substantial cost reducing benefits. The problem with the shared network protocols was the cost to the carriers to build, maintain, and train technical staff. As the footprint of DSL infrastructure expanded, more and more businesses began to adopt the publicly shared data network known as The Worldwide Web. The mass migration off the costly private protocols onto a single standardized IP network led carriers to retire the more expensive privatized network technologies. The next major piece in the equation came when the carrier petitioned the FCC (Federal Communications Commission) to retire the legacy copper networks in favor of the much faster fiber optic infrastructure. This boosted the bandwidth capabilities 1000 X or greater.
The advantages of leasing space in a data center (Otherwise known as moving your data to the cloud) allows the use of multiple shared resources. It also allows the ability to access data from anywhere around the globe with a connection to the internet. (The obvious challenge with this ability is securing private data from malicious activity that we will discuss in much greater detail at a later time and in a separate document) A “Cloud-Based” strategy is designed to provide all the services most small to medium businesses are not able to implement such as the following:
- Multiple fiber optic connections to the data center from diverse carriers and diverse
- entry points.
- Emergency (Power Outage) diesel powered backup generators.
- Calculated in-line DC (Direct Current) battery backup.
- Calculated environmental controls (Temperature Control)
- 24/7/365 Technical staff.
- Secured buildings requiring personal ID.
- Secured data racks or cages.
It is up to each business to evaluate the value of a cloud-based solution vs. a premisebased solution. Currently it is very common to approach the subject via a hybrid solution.
(SOP) – Standard Operating Procedure
It is important to note, while in the process of pricing and ordering a “Network Access Circuit(s)” many carriers will provide a preliminary price based on a computer database of infrastructure resources in the area. This should be acknowledged as strictly “Budgetary Pricing”. The carrier will not provide final pricing until a contract has been signed and submitted. Once the agreement has been received by the carrier, a technician will be dispatched to the location to provide final build plans and pricing. In the event the build cost is within the carriers’ expense threshold, the carrier will proceed to install the circuit. In the event, the pricing is above the expense threshold and additional installation revenue is required to complete the required construction the customer will be presented with the option to pay the additional fees or cancel the agreement without penalty.
Over the years, CT Solutions has created a six (6) step process to design, implement, and manage anything that touches the corporate data network. The first step in the process is for the customer to “Define” what they are seeking to achieve with their network. This step is absolutely necessary. It sets the target. The difficulty with this step is a high percentage of business managers / business owners are not able to articulate how they envision the end product. At the end of the day, they need additional information (i.e.: Training) in what
products and services are available to assist their businesses’ growth through the use of technology.
The misconception is the need for the business managers / business owners to possess a deep knowledge of technology. CT Solutions has provided this information to address technical solutions from the level of a business application. Let me give you a quick
example: If you were in the process of purchasing a video surveillance system and you told me “I want a camera here”. My response to you would be “Don’t tell me where you want a camera, tell me what you want to protect”. Identifying the objective with this type of detail is the best way to accomplish the target goals.
In today’s competitive marketplace, attempting to build a business network without defining the specific requirements of the network gateway is parallel to shooting in the dark. Consider the following questions to determine the best Network Access Strategy is for your business.
What business applications will rely on your corporate data network?
- UCaaS – Unified Communications as a Service (Business Phone System)
- Web Conferencing
- PoS (Point of Sale)
- CRM / ERP System
- Video Surveillance System(s)
- Web Surfing
- FTP File Server
- How much bandwidth will each application require?
- What happens if / when the primary internet connection goes down?
- What monitoring and management capabilities are important to you and the success of your business?
What to Expect – CT Solutions Process & Procedures
In the event you are seeking “Plug & Play / Off the Shelf” internet pricing, CT Solutions offers an automated pricing option.
Download, print, sign, and return a LOA (Letter of Authorization)
